The Unix Security Analyzer for Windows® has two parts: the Configuration Dump Script and the Analyzer.
The Unix configuration analysis tool runs on your workstation to analyze the information extrated by the script. Since most IT Security auditors use Windows® workstations, the analyzer runs on Windows®.
System Requirements:
Windows® XP, 2000, 2003, or Vista.® With .net® 2.0
Please note: The program will install the .net® Framework 2.0 if not already installed.
512MB RAM required, 1GB+ recommended.
Mac, Solaris, Linux, and UNIX users click here to download Mono, which replaces the .net Framework for non-Windows platforms.
Please Note:
This product runs on Microsoft® Windows®, but was not developed by Microsoft® and is not supported by Microsoft®.
Windows, Windows Vista, Window NT, and the Windows logo are registered trademarks of Microsoft Corporation.
- Features
- Instructions
- F.A.Q.
- Case Studies
- Download the Analyzer (a download link will be emailed to you after your purcase)
- Open the Analyzer and click the Download Configuration Extraction Script button to download the extraction script.
- Have the system administrator of the server in question copy the extract script into a new blank directory, review and run the script (the script is a plain batch file to assure administrators that it won't harm their production servers)
- Note that the extraction script is designed for many flavours of Unix. As such, it produces many file not found errors as it runs. This is normal and does not indicate any problems.
- Install/run the analyzer tool onto a separate workstation
- If you encounter an error while installing a new version of the application, do the following:
- Click Start
- Click Control Panel
- Click Add/Remove programs
- Scroll Down and Click Unix Analyzer
- Select Remove the application from this computer and click OK
- Reinstall the analyzer by downloading it again
- once the script runs, copy the generated files to the analysis workstation. If sending to an auditor, I recommend compressing and encrypting the folder in which the script was executed.
- In the Analyzer, click the "Browse" button and select the directory that contains the dump files. The analysis will happen automatically.
How does the program send optional anonymous statistic contributions?
The analyzer program sends the anonymous statistics through a 1024-bit SSL Connection. The analyzer does not send information that may identify the analyzed computer.
Can I prevent the program from sending anonymous statistics?
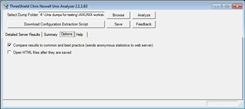
Yes, uncheck the checkbox beside "Compare results to common practice (sends anonymous statistics to web server)" on the Options tab. Please note, however, that disabling this option will prevent the analyzer from comparing your results to common practice.
When and why does the program access the Internet?
The program accesses the Internet three times:
When the program starts, it checks for updates in the background. If an update is available, the next time the program starts, it will ask you if you want to update.
If comparing results to common practice is enabled, anonymous statistics are sent to the web server, which will return a comparison of the analyzed results to common practice. All of these communications are encrypted through 1024-bit SSL encryption
After clicking "more info" beside test results, the program will download help pages from the web server into the "Help" tab.
In 2007, a Fortune 50 conglomerate’s corporate Internal Audit department completed a value stream mapping analysis after replacing manual server review processes with the ThreeShield™ Unix Security Analyzer Tool for Windows®. The analysis found that the ThreeShield™ tools automated 100% of the audit department’s data gathering (which previously took five days of lead time). The tools also reduced server testing by 66%, saving an average of 16 hours of work per domain plus 2.3 additional hours of testing per server.
The study also found that manual server security analysis time is linear (i.e. if one server takes 2.3 hours to review, two servers take 4.6 hours). However, ThreeShield™ tools add efficiency with easy-to-follow reports, so two servers take almost as little time to review as one server.
The month after the department implemented the ThreeShield™ tools, they were able to avoid trips from Connecticut to England and Chile. These avoided travel and entertainment expenses easily recovered the cost of a site license. The audit department also reported that they were able to identify far more control weaknesses than in the past – and report them a week earlier than was possible before implementing the tools!