
|
|
|
Downloads | Contact us
|
|
Computer Assisted Auditing Tools (CAATs)
ThreeShield Information Security initially developed automated security analysis tools to increase efficiency when auditing.
These tools are now in use in government, Fortune 50, educational, and financial organizations including the following:
Some of our tools, such as the Wireless Triangulator Site Survey tool, are publicly offered without charge. These tools were developed to increase the efficiency of our audit services.
The Windows and Unix analyzer tools are free for educational and home use and are licensed for commercial and institutional use. The license fees pay for themselves after one use, given average labour rates.
|
|
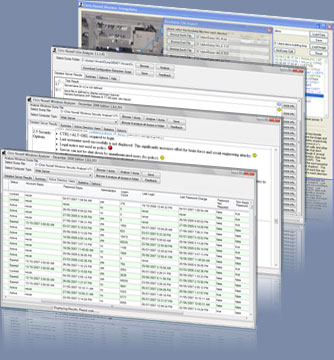
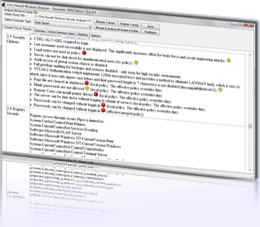
Windows
Security Audit Analysis Tool
Windows security analysis is repetative, time consuming, and requires an extensive
knowledge set. The Windows Security Tool
does the work for you and ensures consistent testing.
The tool includes a comprehensive analysis of over 100 Windows security settings,
extracts Active Directory users, summarizes user attributes, creates a summary spreadsheet,
and compares settings against industry best practice.
|
|
|
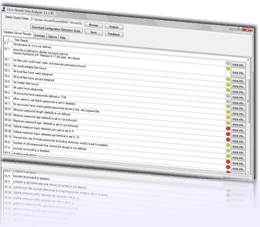
UNIX, Linux, Solaris, HPUX, AIX Security Analysis
*NIX security analysis is repetative and time consuming. The
UNIX security analysis tool does the work for you.
|
|
|
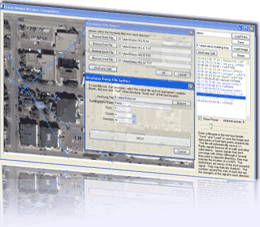
Wireless Triangulator Site Survey
This
wireless site survey tool can be used with any wireless card with an
external directional antenna. It does not require any expensive wireless
infrastructure or comprehensive walk-abouts with a scaled floor plan.
|
|

|
Password Policy Compliance (NIST SP 800-63)
Many security policies -- including those outside of the US Government -- are based on the 800-63 requirements.
This
NIST SP 800-63 Password policy compliance checker helps you to determine if password policies comply with the Electronic
Authentication Guideline. Feel free to use it to test your own systems.
|
|
|
|
LDAP and Active Directory Date Converter
The
LDAP and Active Directory Date Converter converts Active Directory date
fields for pwdLastSet, accountExpires, lastLogonTimestamp, lastLogon, and
badPasswordTime to local time and GMT.
|
|
|
|
Unix Timestamp Date Converter
The
Unix Timestamp Date Converter converts Unix timestamps to local time and
GMT.
|
|
|

|
ThreeShield
Portal
|
|

|
Software News
|
|
|
Windows Security analyzer 1.4.8 features new Active Directory summary feature.
download now
|
|
Unix Security Analyzer now supports
non-english languages.
download now
|
|
NIST SP 800-63 password policy compliance analysis tool now supports NIST, US Government, DoE, NERC, PCI, HIPAA, Alberta Government, and Contractor requirements.
download now
|

|
Advertisers
|
|
|
|
Windows, Windows Vista, Window NT, and the Windows logo are registered trademarks
of Microsoft Corporation. HP-UX is a trademark of Hewlett-Packard Company. AIX is
a trademark of the IBM Corporation. Sun, Java, Solaris, and logos that contain Sun,
Solaris, or Java are trademarks or registered trademarks of Sun Microsystems, Inc.
or its subsidiaries in the United States and other countries.
All text, graphics, and code on this website are Copyright ©1999-2008 ThreeShield
Information Security LLC.
|
|

|








