There are six situations that really require IT Security management support:


We reinforce our short game-like training sessions with practical simulations and tools to help you track real-life progress instead of just quiz completion.
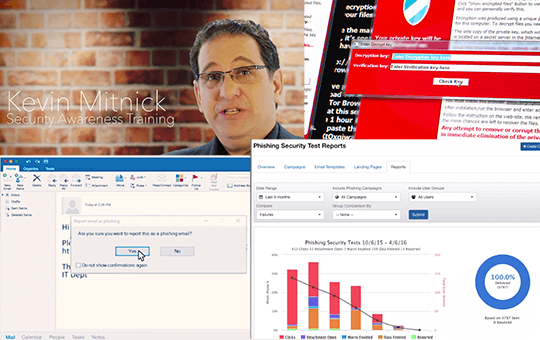
Phishing simulations, "malicious" USB drives, and suspicious reporting plug-ins for Office, Gmail, Lotus, and other email systems change behaviour to secure your business.
Of course, compliance drives a lot of training programs. We have you covered and give you the flexibility of short 5 or 15 minute sessions to keep Information Security Awareness current throughout the year or big-bang sessions to meet last-minute deadlines.
Read more
Are your credit card machine and customer databases properly isolated and protected by a firewall with:
Can you detect and prevent:
If you're relying on consumer-grade routers -- or even most general-purpose enterprise firewalls, you probably aren't meeting PCI credit card compliance requirements or adequately protecting your information. Lavawall™ does all of this in a tiny little box.
For total PCI compliance, we offer PCI training, scanning, policies, procedures, and consulting with the Lavawall™
Ready to protect your business?
|
We'll inform you of significant security events no more than once per week.
MailChimp manages our newsletters. We do not disclose your information to anyone else.
© Copyright 2019 ThreeShield Information Security Corporation